iPU Vanguard: Powering Secure AI and Strategic Edge Computing
Introducing the next frontier in microprocessor design —iPU (Intelligent Processing Unit) architecture. Engineered for national defense, resilient AI, and ultra-efficient energy use.
iPU Secure Processor
The iPU™ (Immunized Processing Unit) is a revolutionary advancement in computer architecture, designed to address modern cybersecurity threats at the hardware level. Unlike traditional processors, the iPU™ integrates security directly into its core architecture, providing real-time, proactive defense against cyber threats without relying on external security software.
Key Features of iPU™:
Hardware-Embedded Security
Creates an isolated secure enclave within the processor to protect sensitive data, significantly reducing the risk of breaches.
Autonomous Threat Neutralization
Detects and inactivates threats instantly, preventing unauthorized access and malicious activity.
Advanced Encryption & Data Integrity
Implements state-of-the-art encryption and authentication protocols to safeguard data confidentiality.
Adaptive High-Performance Computing
Optimized for cloud computing, AI/ML workloads, and IoT devices, ensuring secure, high-speed processing.
No Additional Overhead
Security is built-in at the hardware level, eliminating performance bottlenecks caused by traditional security software.
With cybercrime costs projected to reach $10.5 trillion annually by 2025, the iPU™ represents a transformative shift in cybersecurity, redefining how computing systems are secured, optimized, and powered in the modern digital era.
CALPU™
The CALPU™ (Compiler-Assisted Lookahead Processing Unit) represents a breakthrough in computer architecture, delivering unmatched performance and energy efficiency. By integrating compiler-assisted techniques with lookahead processing, CALPU™ optimizes microprocessor performance and memory management, significantly reducing computational overhead.
Key Innovations of CALPU™:
-
Compiler-Assisted Optimization
During compilation, CALPU™ identifies parallelism opportunities and optimizes resource allocation, enabling faster and more efficient code execution.
-
Lookahead Processing
Predicts and pre-fetches data and instructions in advance, minimizing latency and boosting processing speeds
-
Hardware-Integrated Efficiency
Incorporates specialized circuitry for dynamic data and instruction handling, reducing energy consumption while maximizing computational throughput.
-
Optimized for High-Performance Computing (HPC) and AI:
Enhances execution speeds for applications in scientific computing, artificial intelligence, and advanced analytics, where performance and efficiency are critical.

DARPA iPU-STRIKE:
Strategic AI Compute Under Fire
Engineered for impact. Hardened for chaos.
STRIKE is an iPU-based architecture capable of sustaining intelligent operations in highly contested, resource-constrained environments. With silicon-native defenses and mission-adaptive efficiency, it redefines the limits of secure AI deployment.
Unique Technical Contributions
CIPHERCORE: Immunized Pipelines
for Zero-Trust AI Execution
CIPHERCORE introduces a novel immunized execution pipeline that detects, disrupts, and neutralizes adversarial instruction sequences at runtime. By enforcing behavioral hardening within the microarchitectural fabric, this approach enables tamper-evident, fault-tolerant processing—essential for defense-grade AI applications operating in contested or compromised environments.
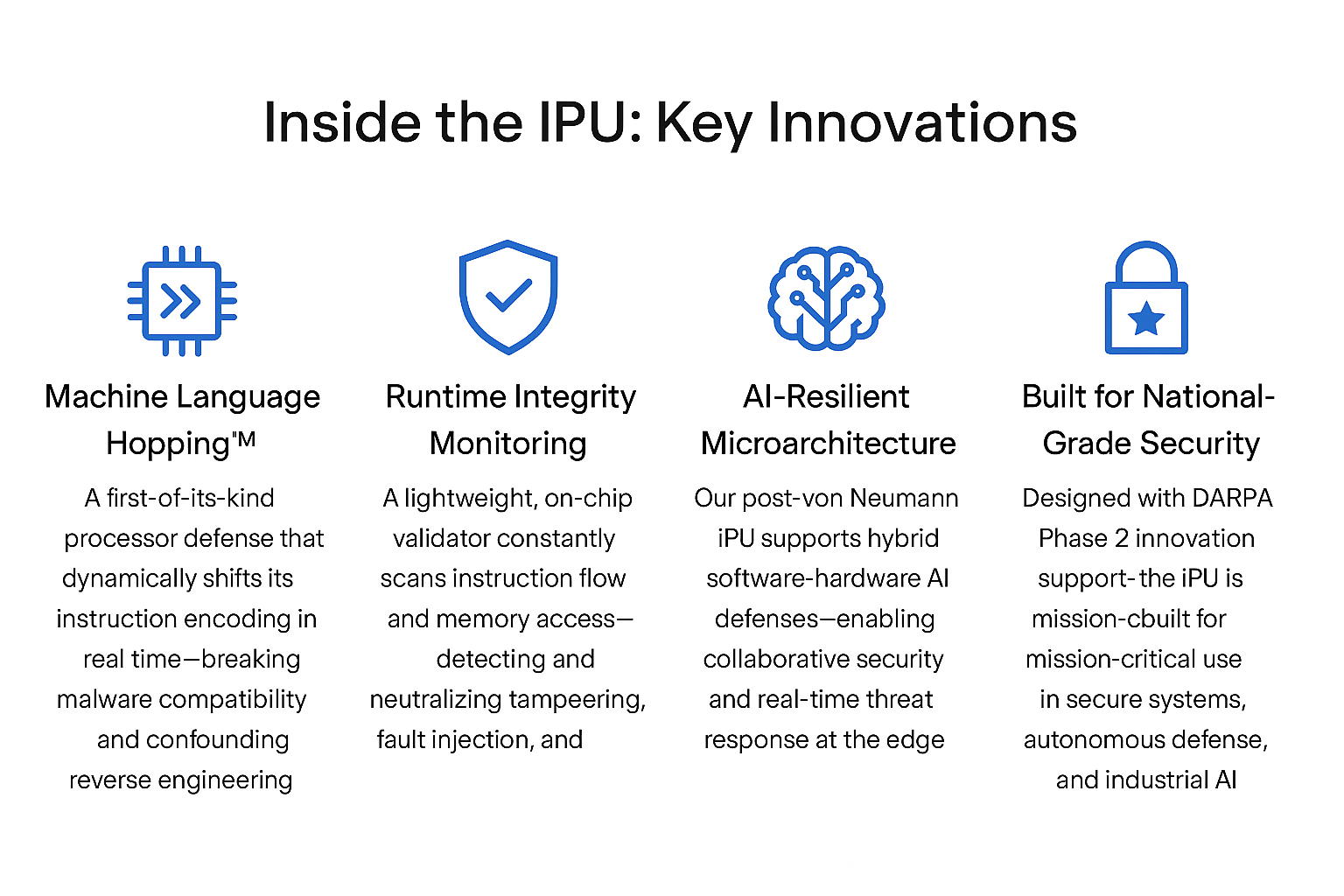
ML-HOP (Machine Language Hopping) is a secure compute innovation that dynamically switches between diverse microinstruction sets during runtime, creating a moving target environment that defeats reverse engineering, injection attacks, and side-channel surveillance. This obfuscation method is adaptive, entropy-aware, and designed for resilient AI co-processing.
Project CHIMERA: Converging Hopping Instruction Sets with Pipeline Immunity
CHIMERA blends machine language polymorphism with pipeline-level anomaly detection, producing a processor architecture that is inherently evasive and self-defensive. Tailored for DARPA-class systems requiring autonomy under fire, CHIMERA offers layered runtime morphing to limit surface area and deny persistent threats at the silicon layer.
Securing the Future of AI—From the Inside Out
The future of secure AI demands processors that are resilient from the inside out.
At AdaptMicroSys, we’re developing the Immunized Processing Unit (iPU) — a new class of processor that protects computation at the hardware and instruction level.
Through DARPA Phase 2 support, our iPU introduces Machine Language Hopping™, runtime integrity validation, and AI-driven countermeasures — enabling post-von Neumann resilience for secure national systems, edge computing, and enterprise AI.
Join the iPU Consortium
We’re building the future of secure, AI-capable computing — and we’re inviting leaders across industry, academia, and government to collaborate.
By joining the iPU Phase 2 Consortium, you’ll gain early insight into groundbreaking secure microarchitecture, contribute to DARPA-aligned innovation, and shape next-generation defense and commercial systems.
Access to early research & IP briefs
Technical collaboration with domain leaders
Co-authorship & proposal partnerships
Visibility in national-scale defense innovation
Benefits List

Let’s Build What’s Next
Have questions or ideas? Whether you're exploring partnerships, funding, or future-proof solutions—let’s connect and shape the next wave of secure, intelligent systems.